Nmmhkkegccagdldgiimedpiccmgmieda
- Nmmhkkegccagdldgiimedpiccmgmieda.crx
- Nmmhkkegccagdldgiimedpiccmgmieda
- Can Chrome Extensions Be Viruses
- Chrome Extension Nmmhkkegccagdldgiimedpiccmgmieda
Quest KACE K1000 (Former Dell Product), allows you to create “customized” inventory rules that provide flexibility to run commands, whether through standard command prompt, or other methods.
For this particular use case, we’re trying to identify what Chrome extensions are installed in our non-domain endpoints that we’re managing. If you are dealing with domain-joined systems, I’d recommend managing these extensions via Google Chrome’s GPO which can be found in my past article.
Problem: Since the textfile CAFADEBUG appeared in one of my document folders, I've had problems with internmittent failure of audio on the internet, and startup has gotten a lot slower. I'm pasting the text that's in this file after SYSINFO below. Outside google search on it names it as a. Page 1 of 2 - Keep having SMART ARP ATTACKS. posted in Virus, Trojan, Spyware, and Malware Removal Help: Hi, I was downloading a torrent a week ago and after that I saw my firewall antivirus.
If you don’t use KACE K1000 in your environment, you can still follow the article and later skip to the “For non-KACE users” section to accomplish the same thing.
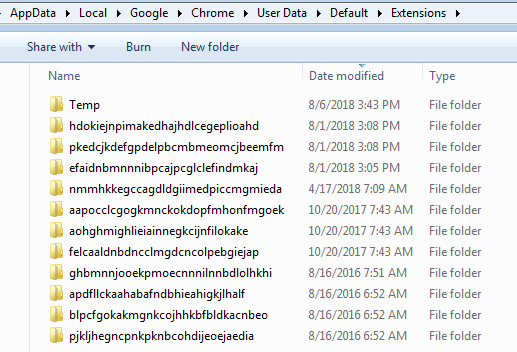
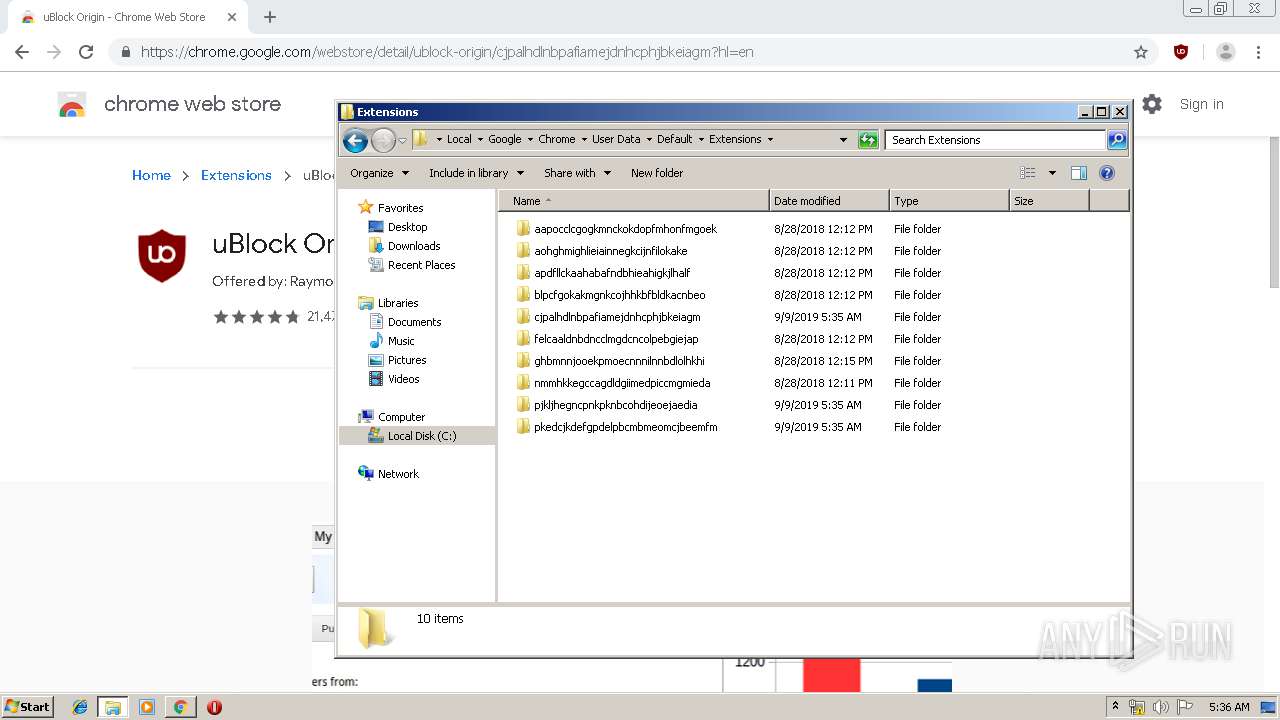
Within KACE we’re going to create a custom inventory rule to return the extensions found under my user appdata directory: C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions
I found the easiest way to do this is to use the dir command within command prompt, with the /b syntax.
File system details View: All details (Selection)- Adds the folder C: Program Files WebDiscoverBrowser Adds the file config.json'=' 15:43, 269 bytes, A Adds the file DelayedStart.lnk'=' 15:43, 970 bytes, A Adds the file isa.dll'=' 14:51, 201216 bytes, A Adds the file Start.lnk'=' 15:43, 932 bytes, A. According to Duo, around 1.7 million users had installed the 70 or so extensions that Kaya initially identified. From there, Google searched and removed a total of 500 or so related extensions.
dir /b “C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions” which returns the following:
Reference for Dir:
| /b | Use this option to show the dir results using “bare” format, which removes the typical header and footer information, as well as all the details on each item, leaving only the directory name or file name and extension. |
The equivalent of powershell is this:
Get-ChildItem -Path “$($env:LOCALAPPDATA)GoogleChromeUser DataDefaultExtensions” -Name
Within Kace, create a custom inventory rule and call it “Google Chrome Extensions”
Navigate to Inventory > Software > Choose Action > New
provide a script name: Google Chrome Extensions
Highlight all of your Windows OS under Supported Operating Systems
Enter the following as the custom inventory rule:
ShellCommandTextReturn(dir /b “C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions”)
Save it!
This will run that command on each endpoint that matches that path and will save the output to the KACE database. Note: This is assuming that your non-domain systems are using the same username. If your usernames are all different throughout the environment, I don’t think this will work. I played around with dir /b “%LOCALAPPDATA%GoogleChromeUser DataDefaultExtensions” but this did not work. I’m assuming it’s because the KACE agent is running as SYSTEM user context.
Moving on, you should see the list of extensions when you look at custom inventory rules results when looking up an endpoint.
Nmmhkkegccagdldgiimedpiccmgmieda.crx
Identifying Extensions:
Google chrome comes with certain extensions by default, in addition there are legitimate extensions such as Adobe PDF readers, or anti-virus extensions added by legitimate products. I spent some time identifying the known extensions via Google Chrome Extensions site; Although some extensions follow an old ID convention or the Google URL store has changed.
Here they are:
| Extension Name | Extension ID |
| Google Slides | aapocclcgogkmnckokdopfmhonfmgoek |
| Google Docs | aohghmighlieiainnegkcijnfilokake |
| Google Calendar #old extension | ejjicmeblgpmajnghnpcppodonldlgfn |
| Google Docs | ghbmnnjooekpmoecnnnilnnbdlolhkhi |
| Google Drive | apdfllckaahabafndbhieahigkjlhalf |
| Youtube | blpcfgokakmgnkcojhhkbfbldkacnbeo |
| Google Sheets | felcaaldnbdncclmgdcncolpebgiejap |
| Google Chrome Web Store | nmmhkkegccagdldgiimedpiccmgmieda |
| Gmail | pjkljhegncpnkpknbcohdijeoejaedia |
| Chromecast | pkedcjkdefgpdelpbcmbmeomcjbeemfm |
| Google Search | coobgpohoikkiipiblmjeljniedjpjpf |
| Google Translate | aapbdbdomjkkjkaonfhkkikfgjllcleb |
I like interacting with the KACE database directly via Mysql Workbench; therefore, I created a SQL script to easily identify the known extensions when creating reports. This made it easy to identify the unknown extensions and also spotting nefarious extensions that shouldn’t be running in the environment:
Note: this assumes that you created the custom inventory software rule and named it “Google Chrome Extensions”.
Here’s the SQL script which will allow you to create an easy-to-read report:
Creating KACE Report for Google Chrome Extensions
Navigate to Reporting > Reports > Select the Drop down menu and select New (SQL)
Provide a title and paste the SQL code provided earlier:
Save it.
Next, run the Report
You should see a report of your endpoints along with the extensions:
As you can see, it’ll be easy to identify unknown extensions.
Although it’s nice that we have visibility over our endpoints, this doesn’t stop the malicious extensions installed from running. The next step is to eradicate those extensions.

Removing unwanted Google Chrome Extensions
Now that we have a good idea of the known good extensions, we can remove all unwanted extensions. To accomplish this, I wrote a Powershell Script and also briefly modified a well known extension written by “bellows” at Spiceworks that removes Google Chrome extensions.
The first Powershell script “GoogleChromeExtensions.ps1” will query the Extensions directory and will exclude the “known expected” extensions and will return only the extensions not found under this list. The list of “unknown or unwanted” extensions will then be passed on to the “Get-ChromeExtensions.ps1” Powershell Script that will start removing each one at a time. This script will remove the extension folder contents for this path, and will also remove registry entries under HKCUSOFTWARE for those extensions.
Here’s the “Get-ChromeExtensions.ps1” script. The only thing I modified was the path to the extensions as Dell KACE will run as SYSTEM and the script won’t work if you don’t deploy it this way. (Note: You may also run scripts as the user context, but I didn’t test this route).
The Modified line is this one: $extension_folders = Get-ChildItem -Path “C:UserspdelgadoAppDataLocalGoogleChromeUser DataDefaultExtensions”
Deploying the script via KACE
Navigate to Scripts > Choose Action > New
Provide a name for the script and make sure you “enable” it.
- Select the Operating system to “Microsoft Windows”.
- Windows run As “Local System”
- Check box for “Allow run without a logged-in user”
- Upload dependencies (GoogleChromeExtensions.ps1) & (Get-ChromeExtensions.ps1)
Under the Tasks section:
On Success : Run a batch file
Provide a script name and paste the following:
powershell.exe powershell.exe -ExecutionPolicy UnRestricted -File .GoogleChromeExtensions.ps1
Save changes, and deploy!
For non-KACE users
You can run these Powershell scripts without specifying a user, and just grabbing the current logged in user via the %LOCALAPPDATA% variable. Ensure you modify the script with other expected extensions or just remove them all!
Here’s the scripts:
and you may use the original “Get-ChromeExtensions.ps1” script along with the one I created which should accomplish the same thing. Easy as 1,2,3.

Conclusion
As mentioned earlier, the scripts deployed will remove unwanted extensions from the provided file path and registry keys; however the extension itself WILL NOT be removed from the Google Chrome browser. When you re-launch the web browser, the folders will re-appear; however, they wont’ have any content and the extension will not be functional. If you browse to the extensions section of Chrome, you will see the extensions with a status of “This extension may have been corrupted” and thus will not be functional as seen in the image below:
Although we’d like to have the extension completely removed from the user’s visibility, this is the next best thing. To my knowledge there isn’t a way to remove the extensions besides having the user do it manually (correct me if I’m wrong, as there might be a better way). The user may always re-install the extensions; however, you can always have an ongoing-job to continue deleting them.
Thanks for reading! Constructive feedback is always appreciated!
One of most obnoxious experiences that most new users of the Linux platform usually face is the inability to find the simplest and yet more effective means of looking up files on their system.
Linux, like almost any other operating system, utilizes several mechanisms to answer search queries for users. Two of the most popular file searching utilities accessible to users are called find and locate.
Now, it is important to note that both search processes work extremely well but nonetheless, the center of this article will be more on the locate utility, which is the more convenient of the two as it uses more efficient ways to quickly process queries inputted by the users.
The locate utility works better and faster than it’s find counterpart because instead of searching the file system when a file search is initiated – Something find does – locate would look through a database. This database contains bits and parts of files and their corresponding paths on your system.
Here are ten simple locate commands to set you up in becoming more productive with your Linux machine.
1. Using locate Command
Firing locate command to look for a file is pretty easy and straightforward. All you need to do is type:
2. Limit Search Queries to a Specific Number
You can limit your search returns to a required number to avoid redundancy with your search results using the -n command.
For example, if you want just 20 results from your queries, you can type the following command:
The results will show the first 20 files that end with .html.
3. Display The Number of Matching Entries
If you want to display the count of all matching entries of file “tecmint“, use the locate -c command.
4. Ignore Case Sensitive Locate Outputs
By default, locate is configured to process queries in a case sensitive manner meaning TEXT.TXT will point you to a different result than text.txt.
To have locate command ignore case sensitivity and show results for both uppercase and lowercase queries, input commands with the -i option.
5. Refresh mlocate Database
Since locate command relies on a database called mlocate. The said database needs to be updated regularly for the command utility to work
efficiently.
To update the mlocate database, you use a utility called updatedb. It should be noted that you will need superuser privileges for this to work properly, is it needs to be executed as root or sudo privileges.
6. Display Only Files Present in Your System
When you have an updated mlocate database**, locate command still produces results of files whose physical copies are deleted from your system.
To avoid seeing results of files not present in your machine at the time of punching in the command, you will need to use the locate-e command. The process searches your system to verify the existence of the file you’re looking for even if it is still present in your mlocate.db.
7. Separate Output Entries Without New Line
locate command’s default separator is the newline (n) character. But if you prefer to use a different separator like the ASCII NUL, you can do so using the -0 command line option.
8. Review Your Locate Database
If you’re in doubt as to the current status of your mlocate.db, you can easily view the locate database statistics by using the -S command.
9. Suppress Error Messages in Locate
Constantly trying to access your locate database does sometimes yield unnecessary error messages stating that you do not have the required privileges to have root access to the mlocate.db, because you’re only a normal user and not the required Superuser.
Nmmhkkegccagdldgiimedpiccmgmieda
To completely do away with these message, use the -q command.
Can Chrome Extensions Be Viruses
10. Choose a Different mlocate Location
If you’re inputting queries looking for results not present in the default mlocate database and want answers from a different mlocate.db located somewhere else in your system, you can point the locate command to a different mlocate database at a different part of your system with the -d command.
Chrome Extension Nmmhkkegccagdldgiimedpiccmgmieda
locate command might seem like one of those utilities that does everything you asked it to do without much of a hustle but in truth, in order for the process to keep its efficiency, the mlocate.db needs to be fed with information every now and then. Failure to do so might render the program a bit useless.
